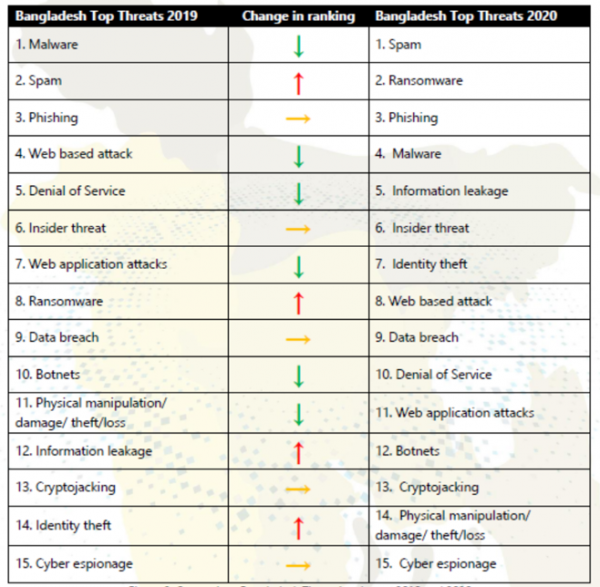
In Bangladesh , Below are the top cyber threats of Bangladesh. If we go through the all threats behavior of exploration, it is clearly identified that, most of the threats occur due to social engineering factors.
What Is Social Engineering
Social Engineering is the psychological manipulation of people into performing actions or divulging confidential information. In terms of Information Security, Social Engineering attack is one of the most common phenomena considering our IT behavioral patterns.
How Attacks relate to Social Engineering
1 Spam Email phishing is the most common type of attack that features social engineering. The target receives a spam email spoofed to look like it was sent by a company or organization the target trusts.
2 Ransomware Ransomware is a type of social engineering that criminals use to infect computers, infiltrate company networks and steal data.
3 Phishing Phishing is the most common type of attack that features social engineering.
4 Malware When malware creators use social engineering techniques, they can lure an unwary user into launching an infected file or opening a link to an infected website. Many email worms and other types of malware use these methods.
5 Information Leakage It might happen through Social Engineering
6 Insider threat Social engineering is a method using interaction between humans to get the access of a system in an illegal way. Due to staff's lack of confidentiality, the confidentiality of records is compromised, data is stolen or financial damage is done. This is insider threat.
7 Identity theft In identity theft terms, 'social engineering' is the act of influencing one to become an identity theft victim through social tactics. Though complex methods are used, the goal remains the same; the identity thief tries to trick you into giving up sensitive information about yourself.
8 Web Based Attack Might occur through Social Engineering (Phishing, Baiting)
9 Data Breach Breach can be done through any human mistake or maniuplation.
10 Denial of Service DDOS is expediated by BotNet
11 Web Application Attack Might Occur through Social Engineering (Phishing, Baiting)
12 Botnet Botnet,that exploits social engineering attacks to spread bots in social networks, has become an underlying threat.
13 Cryptojacking Crypto jacking is common and most form of social engineering, which exploits victims' psychological vulnerabilities.
14 Physical Manipulation Mostly through Social Engineering
15 Cyber Espionage cyber espionage, is the act or practice of obtaining secrets and information without the permission and knowledge of the holder of the information
Common Social Engineering Behaviours
Phishing, Spear Phishing and Whaling Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
It’s a cyber-attack that uses disguised email as a weapon.
Spear phishing is the act of sending and emails to specific and well-researched targets while purporting to be a trusted sender.
A whaling attack is a method used by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals at an organization. Its also known as CEO fraud
Phishing campaigns don't target victims individually—they're sent to hundreds, sometimes thousands, of recipients. Spear phishing, in contrast, is highly targeted and targets a single individual
No alt text provided for this image
- Baiting
Baiting is Phishing’s devious cousin.
As the name suggests, Baiting involves luring an unsuspecting victim with a highly attractive offer playing on fear, greed and temptation to make them part with their personal sensitive data like log-in details.
Baiting attacks are not restricted to online schemes, either. Attackers can also focus on exploiting human curiosity via the use of physical media.
- Botnet
A botnet is a number of Internet-connected devices, each of which is running one or more bots.
By network of Zombie computers infected with malicious software resulting Distributed Denial-of-Service attacks, steal data, send spam, and allow the attacker to access the device and its connection.
- Ransomware
Malicious software that infects your computer, demands a fee (ransom) for your system to work again.
Can be installed through email, IM, websites
Can lock a computer screen or encrypt important, predetermined files
Best Practices to avoid Social Engineering for IT Administrators
- Keep the operating system and installed software up-to-date.
- Regularly uninstall software that is no longer used.
- Use an antivirus program from a reputable company.
- Patching IT infrastructure components in regular, scheduled basis.
- Ensure backup management and Disaster Recovery if possible.
- Use necessary network protections (firewall), Anti-Virus and other security tools
- Equip your organization’s computers with antivirus, data loss prevention, and antispyware software, and update regularly
- Protect all pages of your public websites, not just the payment and registration pages
- Educate employees on cyber threats and how to protect your organization’s data
Best Practices to avoid Social Engineering for Everyone
- Don’t trust the display name or email subject. Don’t reply that mail. Look but don’t click any link and attachment from unknown sender.
- Don’t give personal or company confidential information
- Invoking a sense of urgency or fear is a common phishing tactic. Beware of subject lines.
- Review the signature. Legitimate businesses always provide contact details.
- Use strong passwords. Use two-factor or multi-factor authentication necessarily. Never use default password
- Prohibit the use of public WiFi hotspots