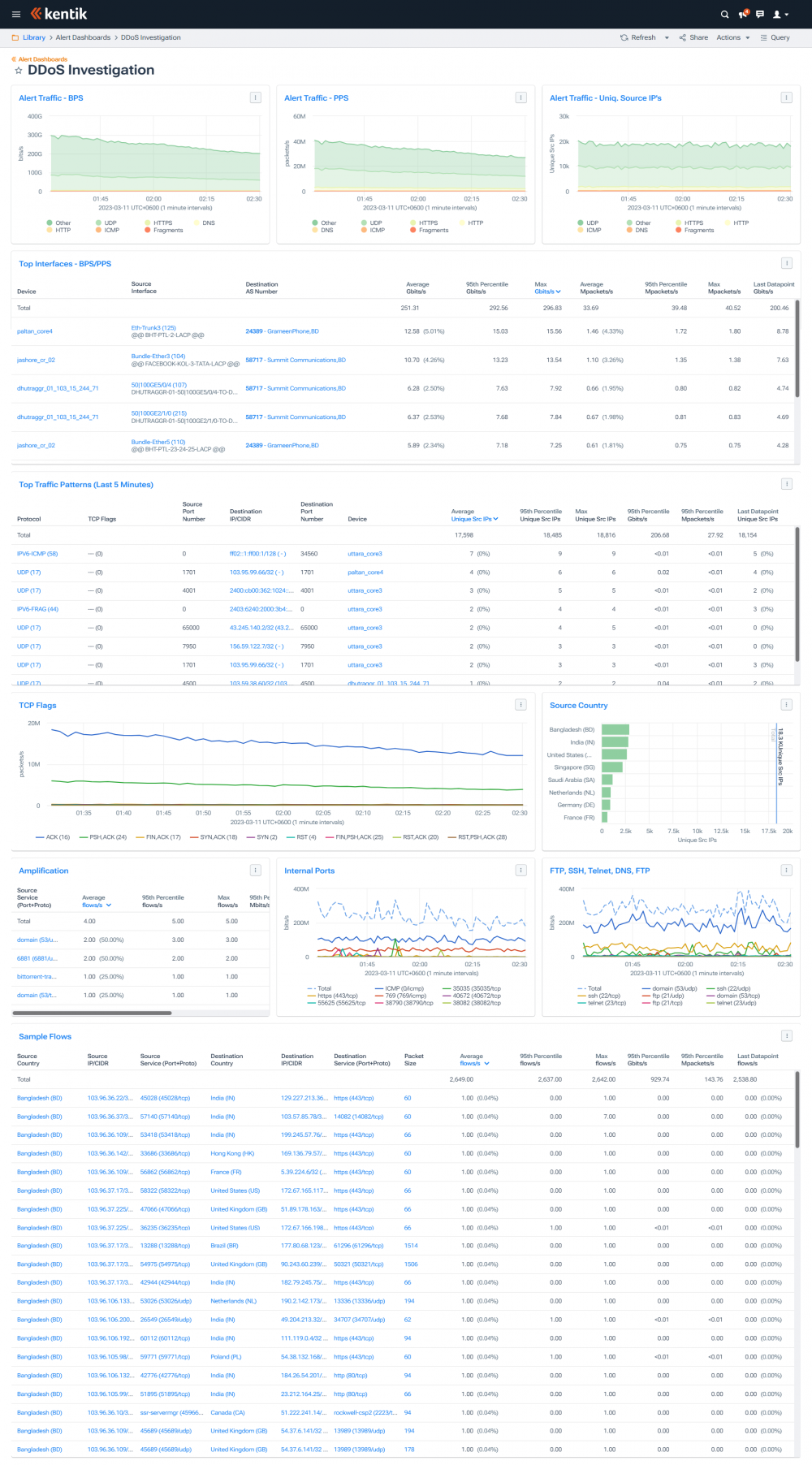
Investigating a DDoS attack on an IIG (International Internet Gateway) network requires a comprehensive approach that involves several steps:
Monitor network traffic: Use network monitoring tools to monitor incoming traffic to the IIG network. Look for any unusual patterns or spikes in traffic that could indicate a DDoS attack.
Identify the type of attack: Determine the type of DDoS attack being used against the IIG network. This could be a volumetric attack, a protocol-based attack, or an application-layer attack.
Block malicious traffic: Use traffic filtering tools to block traffic from the malicious sources. This could include IP blocking, port blocking, or traffic rerouting to the DDoS scrubbing center.
screencapture-portal-kentik-v4-library-dashboards-1790-2023-03-11-02_33_52.pdf